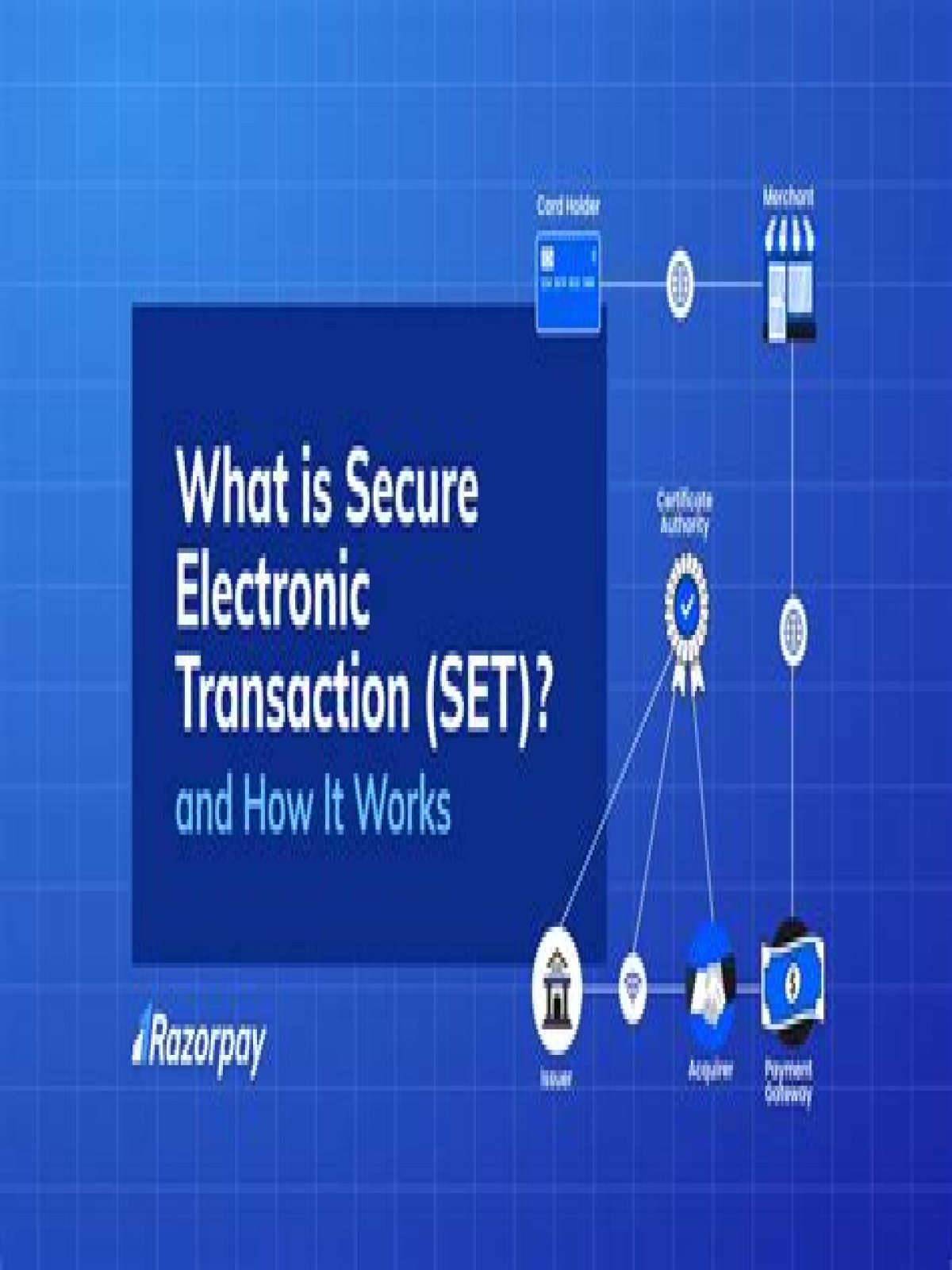
Secure Electronic Transaction is an open-source encryption and security specification designed to protect credit card transactions on the internet. SET provides a secure environment for all the parties that are involved in the e-commerce transaction. It also ensures confidentiality.
- What are the components of secure electronic transaction?
- What do you mean by secure transaction?
- How do you secure transactions?
- How does the bank online transaction process work to secure a transaction?
- What is 3D Secure 2?
- What is a Secure Electronic Transaction (SET)?
- Why do we need secure electronic transaction protocols?
What are the components of secure electronic transaction?
An SET system includes the following components:
- Merchant.
- Cardholder/acquirer.
- Card issuer.
- Payment gateway.
- Certification authority (CA)
- Dual signature: A guaranteed SET data integrity innovation that links two different recipient messages.
How does the user verify the order details in a secure electronic transaction?
The cardholder verifies the merchant and gateway certificates by means of their respective CA signatures and then creates the order information (OI) and payment information (PI). The transaction ID assigned by the merchant is placed in both the OI and PI.
What do you mean by secure transaction?
Generally, a secured transaction is a loan or a credit transaction in which the lender acquires a security interest in collateral owned by the borrower and is entitled to foreclose on or repossess the collateral in the event of the borrower’s default.
How do you secure transactions?
7 Tips for Safe Online Transactions
- Use advanced anti-malware program.
- Watch out for security vulnerabilities in your PC.
- Make sure you are using a secure connection.
- Deal with reputed websites only.
- Use credit cards for online shopping.
- Do not use public computers.
- Set a strong and complex password.
What is 3 D Secure protocol?
3D Secure is a security protocol that is designed to provide an additional layer of security for online credit card and debit card transactions. This protocol was created by Arcot Systems (now CA Technologies) and was first used by Visa to provide improved security for Internet payments.
What are the objectives of secure electronic transaction?
Secure electronic transaction protocols allowed merchants to verify their customers’ card information without actually seeing it, thus protecting the customer against account theft, hacking, and other criminal actions.
What are the different types of security methods you would develop to secure electronic transactions?
Table of Contents
- IP security (IPSec)
- IPSec Architecture.
- Difference between IPSec and SSL.
- Difference between Secure Socket Layer (SSL) and Transport Layer Security (TLS)
- Secure Socket Layer (SSL)
- Transport Layer Security (TLS)
- Secure Electronic Transaction (SET) Protocol.
- Intrusion Detection System (IDS)
What do you learn in secured transactions?
Description: In this course, students glimpse the complex world of commercial finance that lurks behind most facets of modern life. This course examines the treatment of secured transactions under Article 9 of the Uniform Commercial Code.
How does the bank online transaction process work to secure a transaction?
Basically, when the customer places an order on the merchant’s website, the payment gateway securely gathers and stores the transaction data, which is processed and forwarded to the financial institution and to the credit card networks, which, in turn, transfer the encrypted information to the customer’s card issuing …
What is 3D Secure 2?
3D Secure 2 is an industry authentication protocol that provides the default mechanism to perform strong (two-factor) authentication. It aims to reduce fraud and enhance security in online card payments. Customers can authenticate their identity without disturbing their user experience within the merchant’s website.
How many stages are there in 3D security protocol?
In addition, 3D Secure is limited by the mass adoption of this authentication method being crucial in the 3 stage process of making a transaction.
What is a Secure Electronic Transaction (SET)?
Remember that a secure electronic transaction is not a payment system; it is a set of security protocols and format that ensures that using online payment transaction on the internet is secure. Secure Electronic Transaction is also called SET.
Why do we need secure electronic transaction protocols?
The development of secure electronic transaction protocols were a response to the emergence and growth of e-commerce transactions, especially consumer-driven purchases over the Internet. Conducting business online was a new phenomenon in the mid-1990s.
What is Secure Transaction Technology (STT)?
It uses different encryption and hashing techniques to secure payments over the internet done through credit cards. The SET protocol was supported in development by major organizations like Visa, Mastercard, Microsoft which provided its Secure Transaction Technology (STT), and Netscape which provided the technology of Secure Socket Layer (SSL).
What are the steps taken during an electronic transaction?
The following are the ten steps taken during an electronic transaction: In the first two message exchanges between the consumer and merchant, the consumer and merchant signal their intention to do business. They then exchange certificates and establish a transaction ID number.